Infrastructure as Code (IaC) has emerged as a cornerstone for efficiently managing and provisioning infrastructure. Among the many tools available, Terraform has gained unparalleled popularity, offering a declarative approach to defining and deploying infrastructure.
But as organizations increasingly embrace IaC to achieve scalability, consistency, and agility, a critical challenge emerges: how to ensure compliance and authorization for infrastructure changes.
With rapid and dynamic transformations in the digital realm, maintaining regulatory adherence, security standards, and internal policies becomes increasingly challenging.
In this article, we delve into the intricacies of compliance in the context of infrastructure changes, exploring the significance of enforcing regulatory frameworks and safeguarding against potential risks associated with evolving infrastructure landscapes.
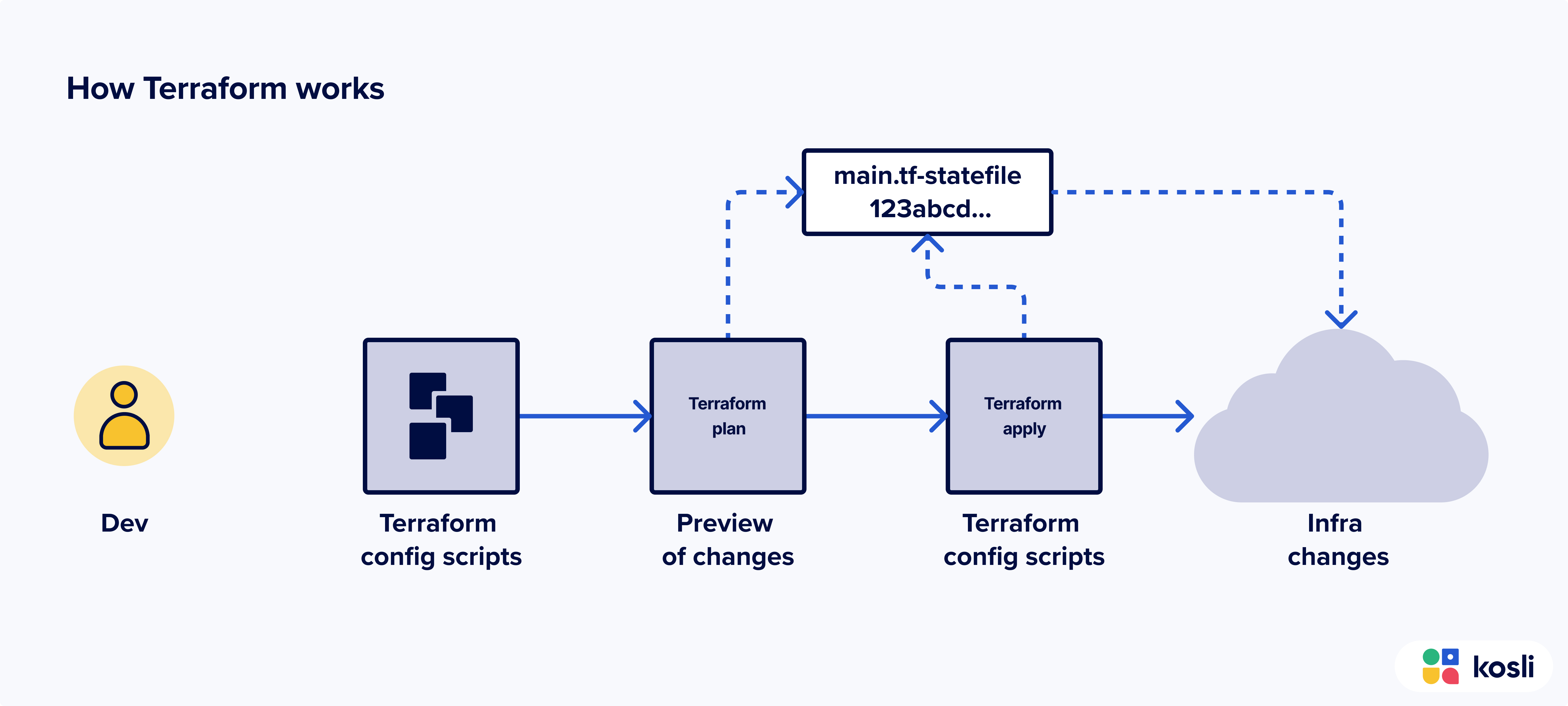
How Terraform works
Terraform users define their desired infrastructure state using declarative configuration files, known as Terraform scripts. These scripts articulate the desired configuration, specifying resources like servers, networks, and storage in a human-readable format.
The key concept in Terraform is the “desired state.” Users describe the infrastructure they want, and Terraform ensures that the actual infrastructure matches this specified state. Terraform employs a plan and apply workflow: users create a Terraform plan, a preview of changes, and then apply it to execute those changes.
The Terraform state is a crucial component that tracks the current state of the infrastructure. It stores metadata about resources and their dependencies, allowing Terraform to understand how to modify or destroy resources without compromising the overall infrastructure integrity. The state file serves as a bridge between the desired and actual states, ensuring that Terraform actions align with the defined configuration.
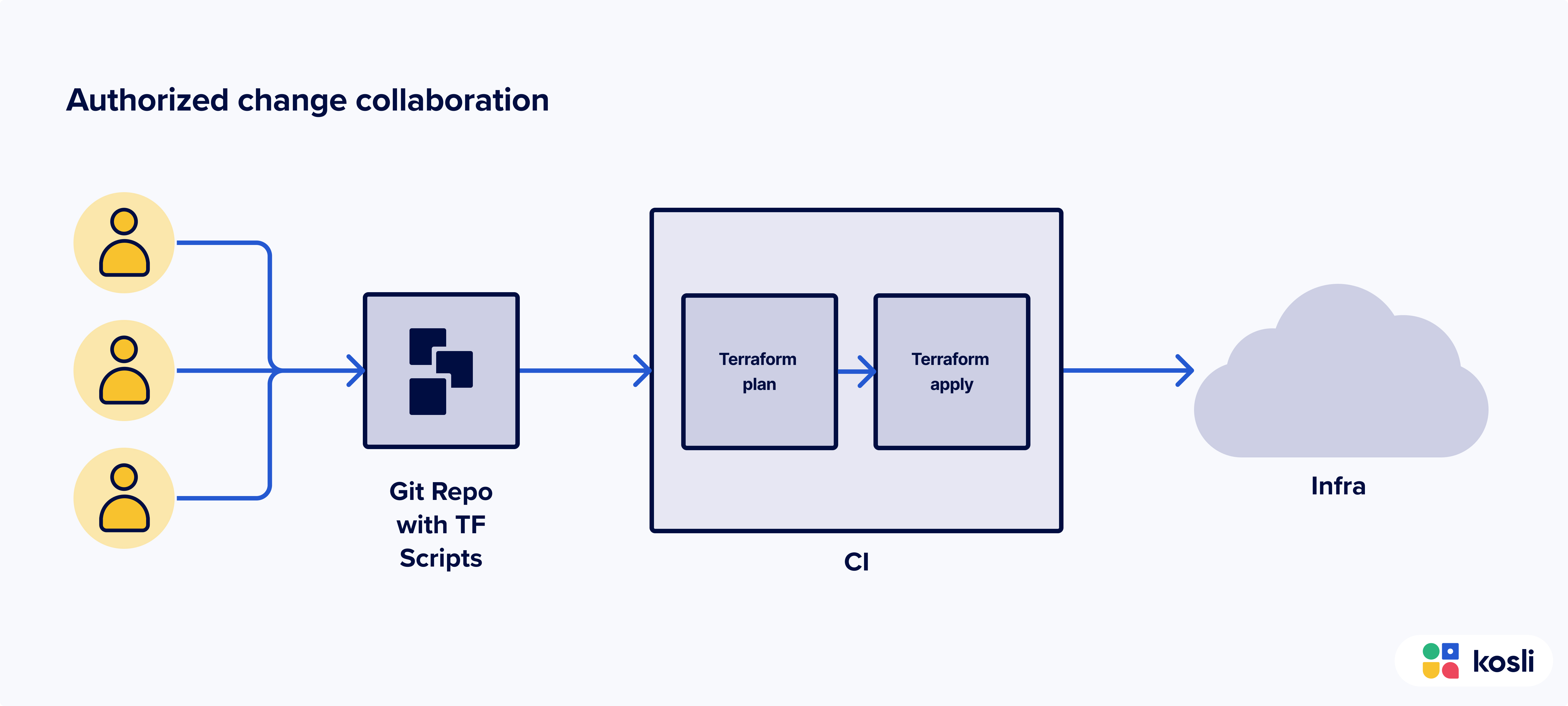
Establishing a path for authorized Terraform changes
Collaborating on Terraform projects is streamlined through the use of version control systems like Git, enabling teams to work cohesively on infrastructure configurations. Storing the Terraform scripts and defining the desired state of the infrastructure in a Git repository allows for efficient collaboration, version tracking, and history management.
Continuous Integration (CI) tools can be configured to automatically validate, plan and apply Terraform changes upon code commits, ensuring consistent and error-free deployments.
Processes for infrastructure changes could be implemented in a version control system and CI workflows. For instance, protecting the main branch from direct commits (i.e. changes go via pull requests only) and linting and testing the terraform scripts in CI. This establishes the path for authorized changes.
The problem with unauthorized changes
Unauthorized changes pose a significant challenge, potentially undermining the carefully crafted CI/CD processes. When modifications are made outside the established CI workflow, they bypass crucial checks and reviews, leading to unvalidated alterations to the infrastructure.
This can result in a variety of issues, such as introducing vulnerabilities, violating compliance standards, or disrupting the overall stability of the environment. Unauthorized changes not only compromise the integrity of the infrastructure but also hinder the ability to trace, audit, and manage alterations effectively.
There are two common sources for unauthorized changes.
- Type 1 changes are made directly to the infrastructure through cloud consoles, CLI tools or API endpoints, bypassing the Terraform workflows. These changes, while immediately impacting the infrastructure, remain outside the realm of Terraform’s control. Leveraging Terraform drift detection becomes crucial in identifying and rectifying such unauthorized changes. By automating drift detection to run on a regular schedule, you can proactively mitigate the risk associated with these changes, maintaining the desired state and reinforcing the security and compliance of the infrastructure.
- Type 2 changes are made with Terraform, but circumvent the established CI workflows. An example is a developer directly executing “terraform apply” from their local machine. Such changes, while performed with Terraform, can be challenging to detect since they update the Terraform state files, rendering conventional Terraform drift detection ineffective.
Tracking unauthorized Infrastructure as Code changes with Kosli
The roadmap for controlling IaC changes without frictions is as follows:
- Enforce a process for authorized changes: Ensure that every change follows a specific process by integrating it into the CI workflow
- Track authorized changes: Record all IaC changes in Kosli to provide a transparent record of adherence to the desired process over time.
- Automate and track drift detection: Automate drift detection and correction execution and record its outcome in Kosli to address Type 1 Unauthorized changes.
- Monitor your Terraform State File: setup Kosli to monitor changes to the Terraform state file. This allows the tracking and attribution of state file modifications to their respective sources.
- Alerting for Type 2 Unauthorized Changes: Let Kosli detect unauthorized changes of Type 2 and receive alerts for it. This provides proactive notification and enables prompt corrective actions.
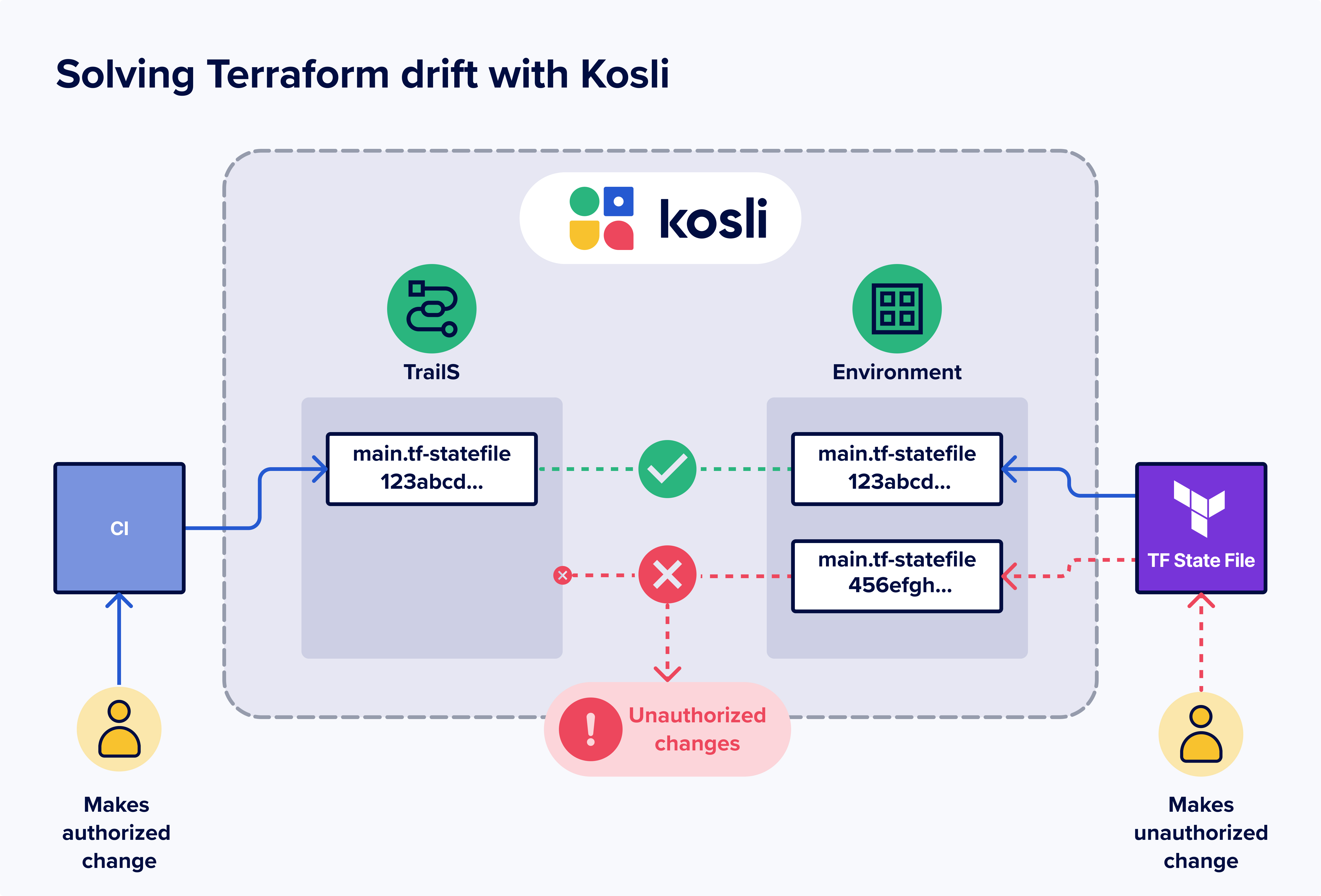
By recording authorized changes, and their effect (the terraform state file SHA256 fingerprint after applying the changes), and monitoring the SHA256 fingerprint of the Terraform state file, Kosli can detect an unauthorized IaC change based on whether the expected state file fingerprint matches the actual.
Integrating Terraform drift detection and CI workflows for automated Terraform processes with Kosli will help you to detect and resolve unauthorized changes. By combining these elements, this approach ensures not only the detection and resolution of various unauthorized changes but also establishes a robust audit trail, making your infrastructure changes always audit-ready.