If you’re delivering software in a regulated environment, or deploying to a critical application or device, ensuring the security of your software code and dependencies is essential. One of the most popular tools for achieving this is Snyk, which gives developers the ability to find and fix vulnerabilities as part of their development workflow.
Shifting left on security with Snyk is obviously great, but if you have to go through a security audit you also have to be able to prove that everything was Snyk scanned before it was deployed to production. How do you get the proof for that? And how can you be alerted if there’s a workload in production that hasn’t been scanned?
This is where Kosli’s Snyk integration for evidence recording can help. In this post you’ll discover how Kosli gathers the evidence for your Snyk scans and alerts you when something is deployed without one.
How to record Attestations for Snyk evidence
Kosli’s flow attestations allow you to record evidence that pipeline events occurred for a given commit or artifact. These immutable, append-only records enable you to create a provable chain of custody from commit to production. With our Evidence Vault, you can also upload results files as supporting evidence, such as Snyk security scans.
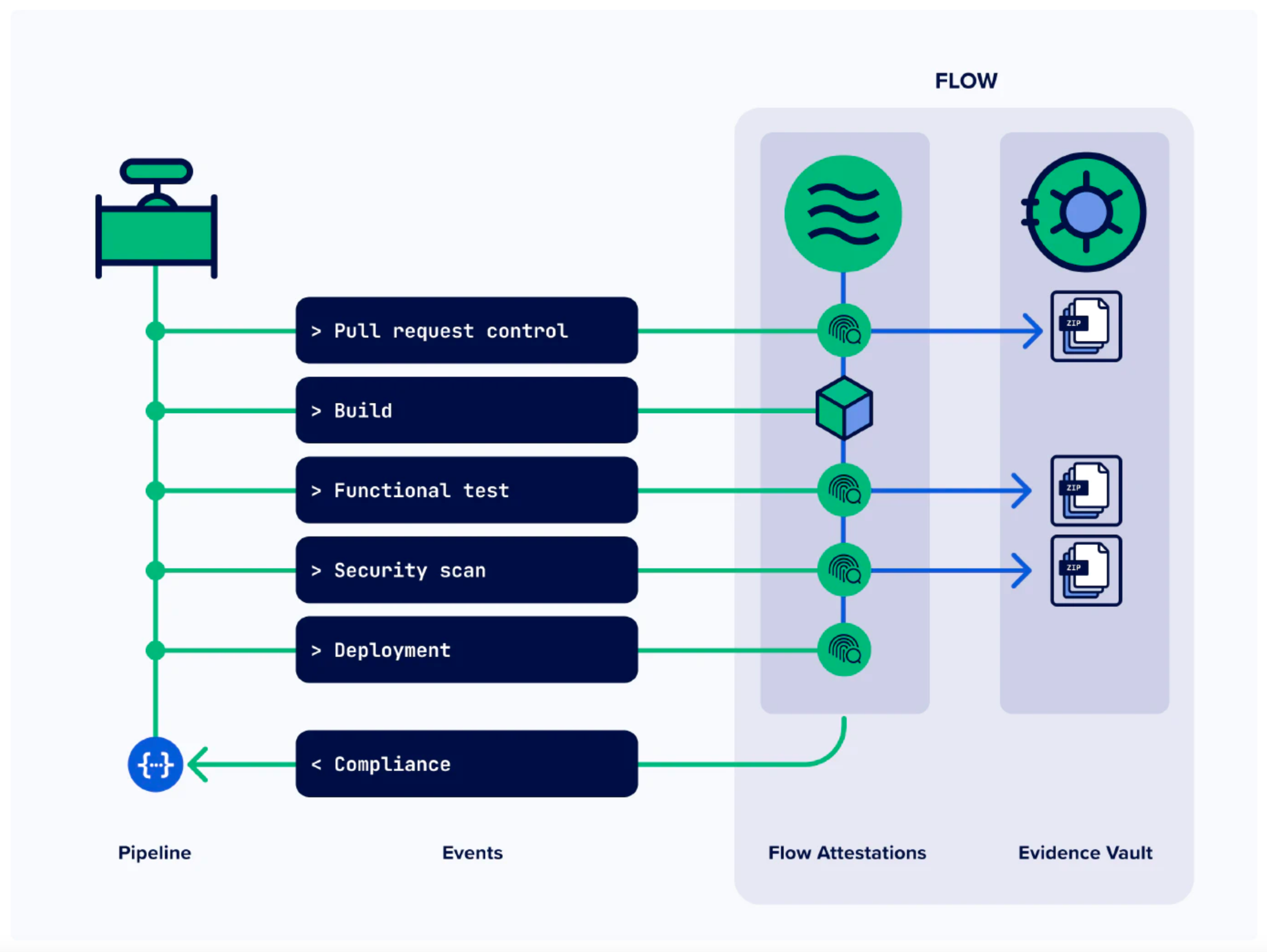
If you are already recording software builds, and performing Snyk scans in your pipelines, then you can simply report the snyk scan in your pipeline. Kosli works with any CI system, but here’s an example of how it might look in GitHub:
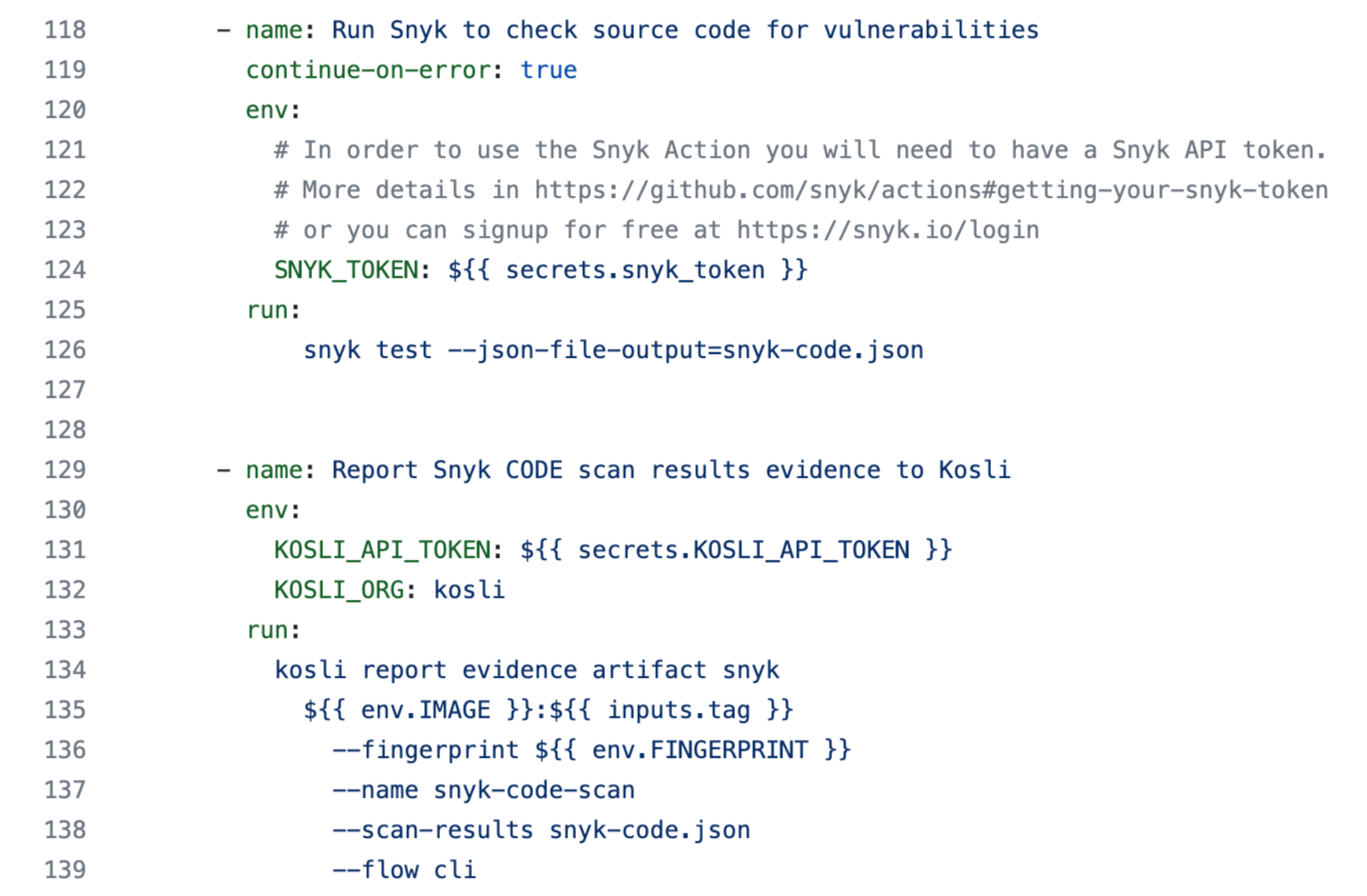
This attestation will now be recorded against your artifact in Kosli. The scan results json file is also parsed and uploaded to Kosli’s Evidence Vault. If no vulnerabilities are detected, the evidence is reported as compliant. However, if vulnerabilities are found, the evidence is reported as non-compliant and the artifact becomes non-compliant.
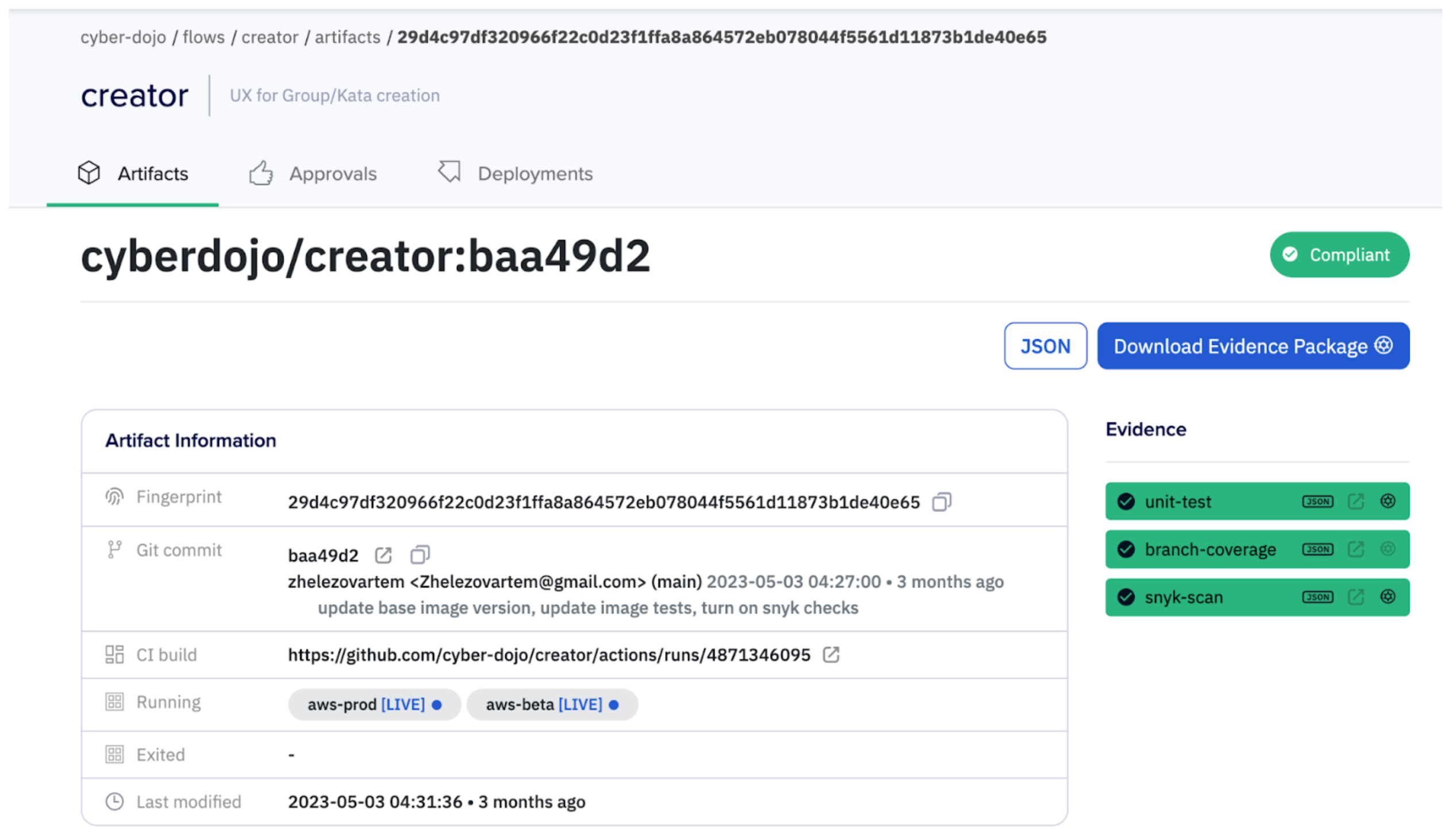
You will also see the Snyk scan attestation in the history for the artifact, forming part of the chain of custody.
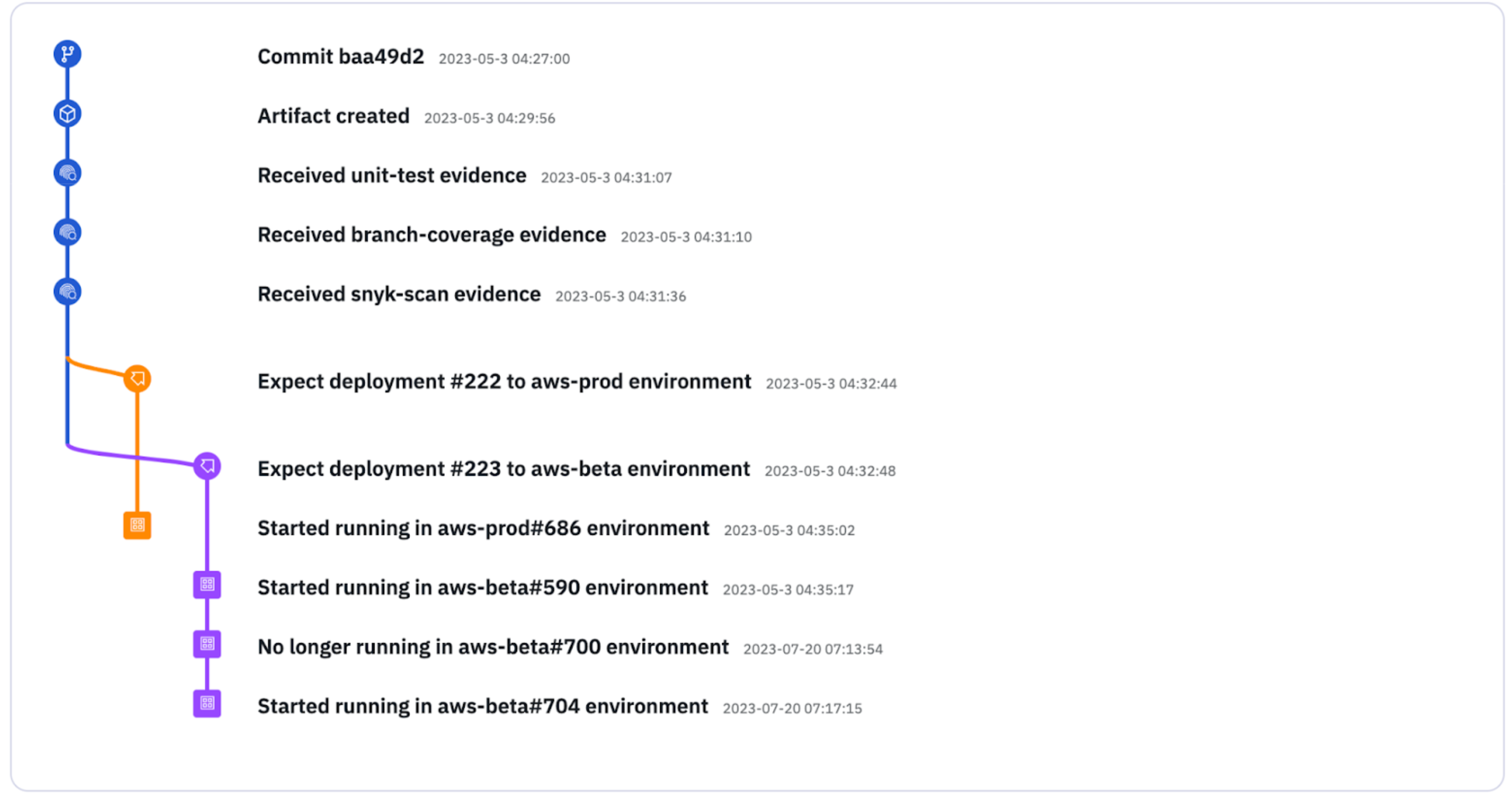
Tracking Snyk usage across pipelines
If you are interested in verifying compliance with a security standard like SOC2 or ISO27001, you will likely have a company policy which states a mandatory code and dependency analysis. This will be something you will need to prove to the auditors, who will want to see evidence that this occurred for every change to your system. In large, distributed teams it can be quite a headache to figure out which pipelines and repos comply, and more importantly, where and how to find the proof.
This is where Kosli’s controls view can help. On this page you can view all of your artifact flows, and what attestations are being recorded. You get an instant, bird’s eye view of where you have evidence, and more importantly, where the gaps are.
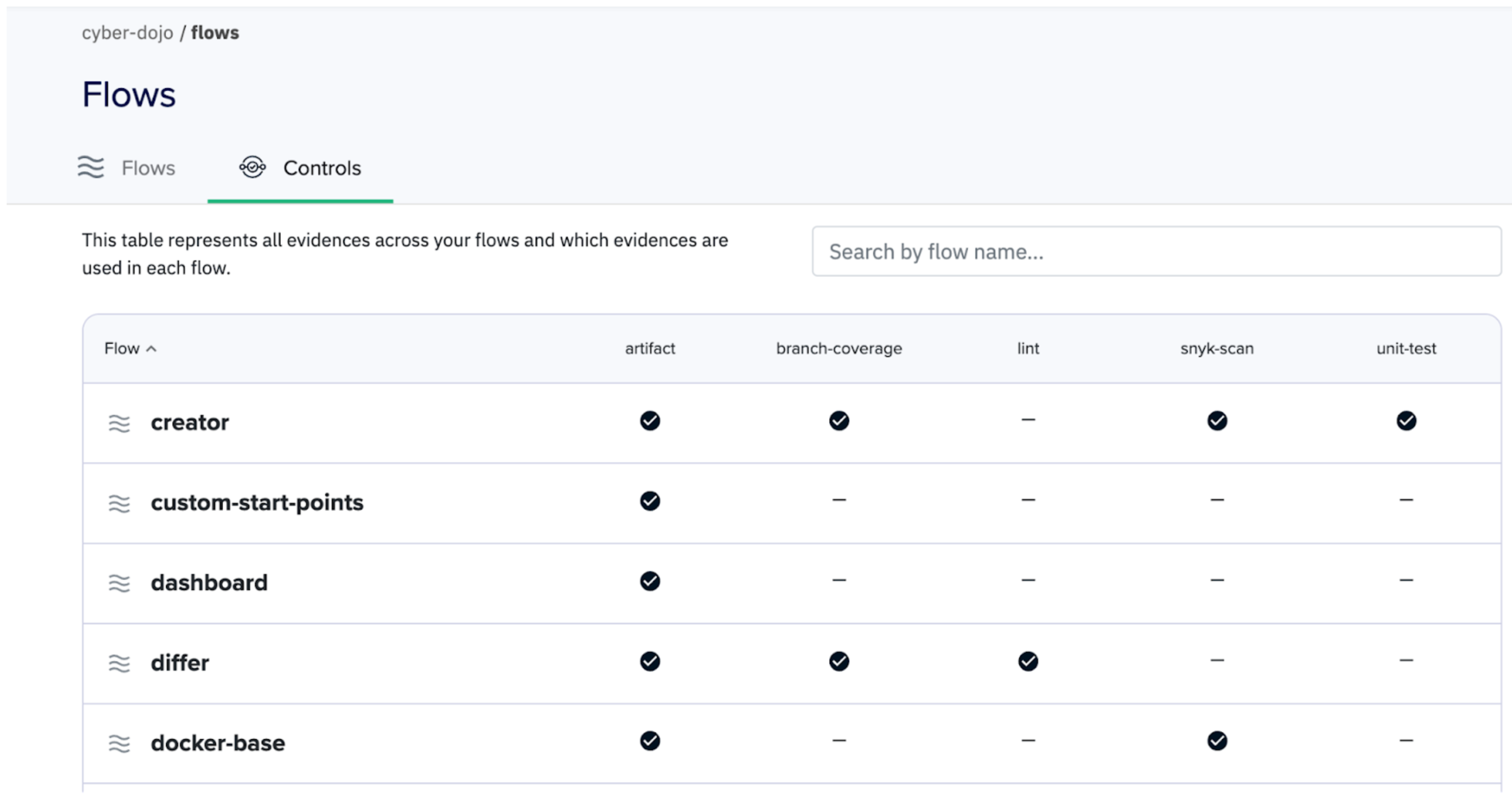
Even better, you can use this data to create deployment controls to ensure that only artifacts with passing security scans are allowed into your environments.
How to detect unscanned workloads
Securing your delivery pipelines is a great start, but to be really sure you are compliant a golden path isn’t enough. What happens if a new pipeline is set up that doesn’t follow the requirements? Or someone with access to production manually deploys a local build?
With environment recording Kosli keeps a forensic history of what is running in your environments over time. Now you can prove to an auditor that only scanned software that has been through the approved channels has been running. And, to make the auditor extra happy, Kosli can provide a CSV export of all the evidence they could ever wish to see.
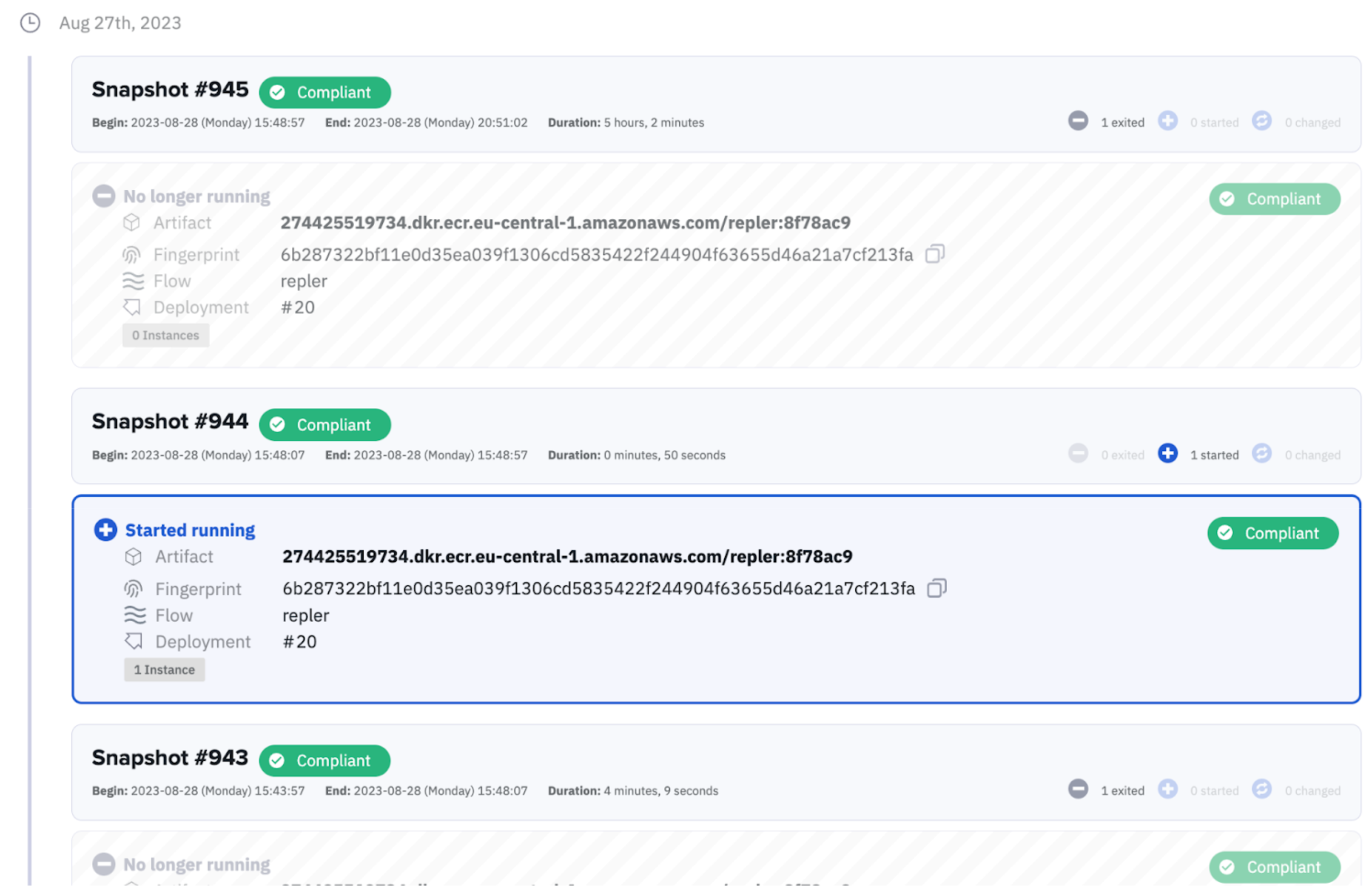
How to audit the evidence
When audit time comes around you have full records of what has been running in your systems together with a provable chain of custody. And the attestations and evidence can be downloaded from the Kosli Evidence Vault at any time.
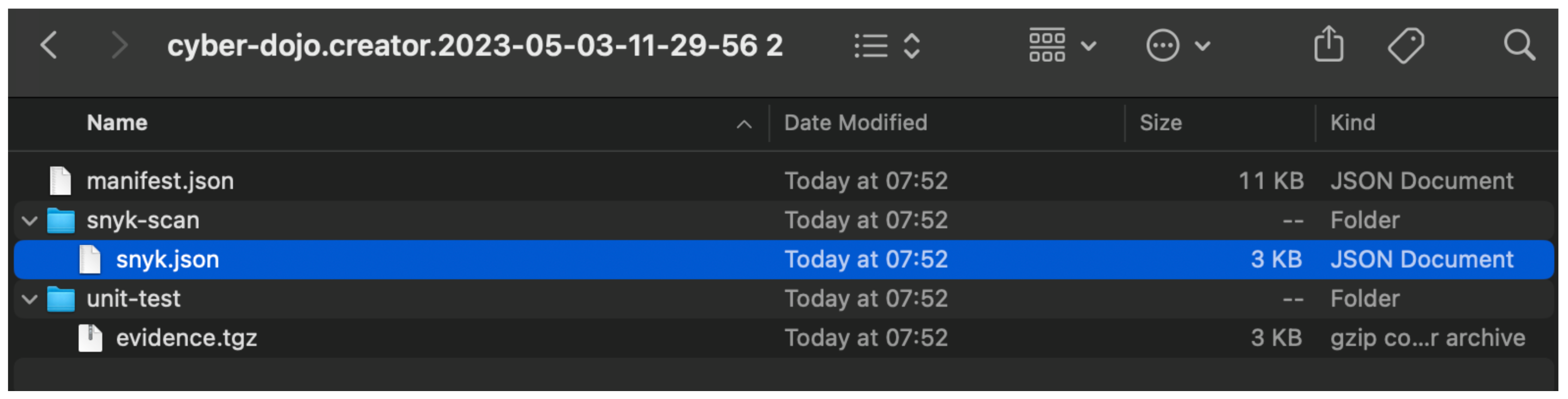
You always have the proof you need when the auditors show up at the touch of a button.
Summary
In the post you were able to see how easy it is to keep track of all your Snyk scan evidence, allowing you to avoid the pains associated with security audits. If you have any questions or feedback, feel free to reach out to us in our Slack community any time!
Keep an eye out for my next post where I’ll show you how to use Kosli’s environment monitoring + Snyk to continuously scan all of your production workloads! To be sure you won’t miss it, sign up for our newsletter and be notified when we publish ;-)
















